A) Three; security management, Security Gateway, and endpoint security
B) Three; Security gateway, endpoint security, and gateway management
C) Two; security management and endpoint security
D) Two; endpoint security and Security Gateway
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Each cluster has __________ interfaces.
A) Five
B) Two
C) Three
D) Four
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The _________ software blade enables Application Security policies to allow, block, or limit website access based on user, group, and machine identities.
A) Application Control
B) Data Awareness
C) URL Filtering
D) Threat Emulation
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which policy type is used to enforce bandwidth and traffic control rules?
A) Threat Emulation
B) Access Control
C) QoS
D) Threat Prevention
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which option, when applied to a rule, allows all encrypted and non-VPN traffic that matches the rule?
A) All Site-to-Site VPN Communities
B) Accept all encrypted traffic
C) All Connections (Clear or Encrypted)
D) Specific VPN Communities
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
A) fwd
B) fwm
C) cpd
D) cpwd
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem? Choose the BEST answer. 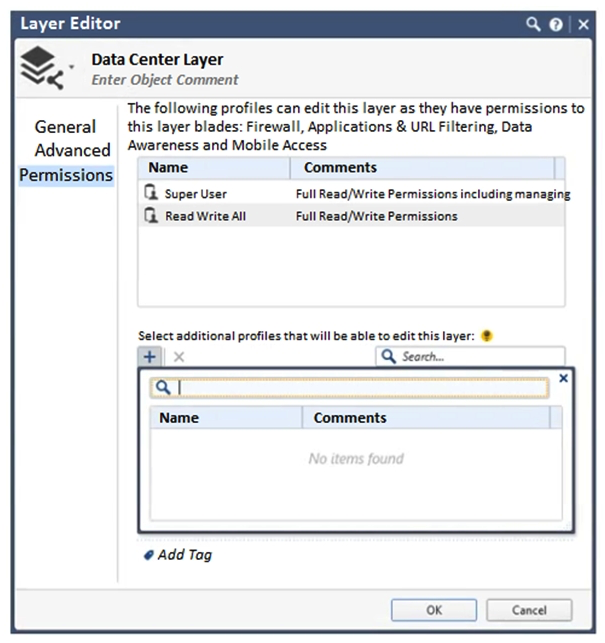
A) "Edit layers by Software Blades" is unselected in the Administrator Permission Profile
B) There are no Administrator Permission Profiles available and you need to create one first.
C) All Administrator Permission Profiles are in use.
D) There are no Administrator Permission Profiles defined with limited access privileges.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which icon indicates in the WebUI that read/write access is enabled?
A) Pencil
B) Padlock
C) Book
D) Eyeglasses
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
On R80.10 when configuring Third-Party devices to read the logs using the LEA (Log Export API) the default Log Server uses port:
A) 18210
B) 18184
C) 257
D) 18191
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blank: Service blades must be attached to a ______________.
A) Security Gateway
B) Management container
C) Management server
D) Security Gateway container
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted communication. Which of the following methods is BEST to accomplish this task?
A) Use SmartView Tracker to follow his actions by filtering log entries that feature the WinSCP destination port. Then, export the corresponding entries to a separate log file for documentation.
B) Use SmartDashboard to add a rule in the firewall Rule Base that matches his IP address, and those of potential targets and suspicious protocols. Apply the alert action or customized messaging.
C) Watch his IP in SmartView Monitor by setting an alert action to any packet that matches your Rule Base and his IP address for inbound and outbound traffic.
D) Send the suspect an email with a keylogging Trojan attached, to get direct information about his wrongdoings.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The R80 feature ________ permits blocking specific IP addresses for a specified time period.
A) Block Port Overflow
B) Local Interface Spoofing
C) Suspicious Activity Monitoring
D) Adaptive Threat Prevention
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the default shell for the command line interface?
A) Expert
B) Clish
C) Admin
D) Normal
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
A) Manage and Command Line
B) Logs and Monitor
C) Security Policies
D) Gateway and Servers
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the order of NAT priorities?
A) Static NAT, IP pool NAT, hide NAT
B) IP pool NAT, static NAT, hide NAT
C) Static NAT, automatic NAT, hide NAT
D) Static NAT, hide NAT, IP pool NAT
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a back up method?
A) Save backup
B) System backup
C) snapshot
D) Migrate
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which one of the following is true about Threat Extraction?
A) Always delivers a file to user
B) Works on all MS Office, Executables, and PDF files
C) Can take up to 3 minutes to complete
D) Delivers file only if no threats found
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
A) Symmetric routing
B) Failovers
C) Asymmetric routing
D) Anti-Spoofing
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How do you configure the Security Policy to provide uses access to the Captive Portal through an external (Internet) interface?
A) Change the gateway settings to allow Captive Portal access via an external interface.
B) No action is necessary. This access is available by default.
C) Change the Identity Awareness settings under Global Properties to allow Captive Policy access on all interfaces.
D) Change the Identity Awareness settings under Global Properties to allow Captive Policy access for an external interface.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is TRUE regarding Gaia command line?
A) Configuration changes should be done in mgmt_cli and use CLISH for monitoring, Expert mode is used only for OS level tasks.
B) Configuration changes should be done in expert-mode and CLISH is used for monitoring.
C) Configuration changes should be done in mgmt-cli and use expert-mode for OS-level tasks.
D) All configuration changes should be made in CLISH and expert-mode should be used for OS-level tasks.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Showing 201 - 220 of 676
Related Exams