A) Data Loss Prevention (DLP) shared policy
B) Geo policy shared policy
C) Mobile Access software blade
D) HTTPS Inspection
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blanks: VPN gateways authenticate using ___________ and ___________ .
A) Passwords; tokens
B) Certificates; pre-shared secrets
C) Certificates; passwords
D) Tokens; pre-shared secrets
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An Endpoint identity agent uses a ___________ for user authentication.
A) Shared secret
B) Token
C) Username/password or Kerberos Ticket
D) Certificate
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You are unable to login to SmartDashboard. You log into the management server and run #cpwd_admin list with the following output: 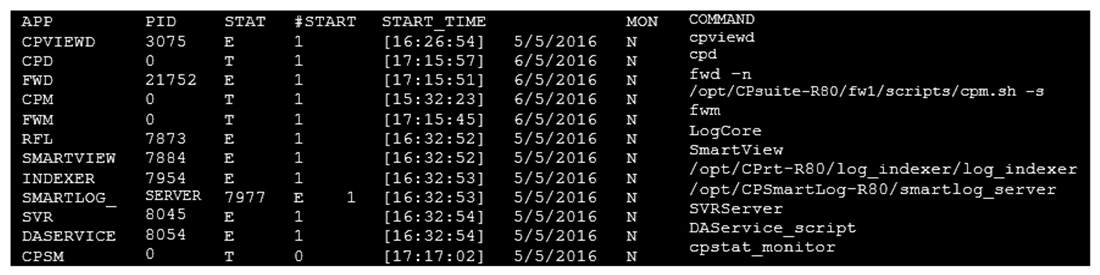 What reason could possibly BEST explain why you are unable to connect to SmartDashboard?
What reason could possibly BEST explain why you are unable to connect to SmartDashboard?
A) CDP is down
B) SVR is down
C) FWM is down
D) CPSM is down
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Kofi, the administrator of the ALPHA Corp network wishes to change the default Gaia WebUI Portal port number currently set on the default HTTPS port. Which CLISH commands are required to be able to change this TCP port? 
A) set web ssl-port <new port number>
B) set Gaia-portal <new port number>
C) set Gaia-portal https-port <new port number>
D) set web https-port <new port number>
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
To create policy for traffic to or from a specific geographical location, use the _____________.
A) Data Loss Prevention (DLP) shared policy
B) Geo policy shared policy
C) Mobile Access software blade
D) HTTPS inspection
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The tool _______ generates an R80 Security Gateway configuration report.
A) infoCP
B) infoview
C) cpinfo
D) fw cpinfo
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following is NOT a valid option when configuring access for Captive Portal?
A) From the Internet
B) Through internal interfaces
C) Through all interfaces
D) According to the Firewall Policy
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which tool is used to enable cluster membership on a Gateway?
A) SmartUpdate
B) cpconfig
C) SmartConsole
D) sysconfig
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When Identity Awareness is enabled, which identity source(s) is(are) used for Application Control?
A) RADIUS
B) Remote Access and RADIUS
C) AD Query
D) AD Query and Browser-based Authentication
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What object type would you use to grant network access to an LDAP user group?
A) Access Role
B) User Group
C) SmartDirectory Group
D) Group Template
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Tom has been tasked to install Check Point R80 in a distributed deployment. Before Tom installs the systems this way, how many machines will he need if he does NOT include a SmartConsole machine in his calculations?
A) One machine, but it needs to be installed using SecurePlatform for compatibility purposes.
B) One machine
C) Two machines
D) Three machines
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A Check Point Software license consists of two components, the Software Blade and the Software Container. There are ______________ types of Software Containers: ______________.
A) Three; Security Management, Security Gateway, and Endpoint Security
B) Three; Security Gateway, Endpoint Security, and Gateway Management
C) Two; Security Management and Endpoint Security
D) Two; Endpoint Security and Security Gateway
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which one of the following is the preferred licensing model?
A) Local licensing because it ties the package license to the IP-address of the gateway and has no dependency of the Security Management Server.
B) Central licensing because it ties the package license to the IP-address of the Security Management Server and has no dependency of the gateway.
C) Local licensing because it ties the package license to the MAC-address of the gateway management interface and has no Security Management Server dependency.
D) Central licensing because it ties the package license to the MAC-address of the Security Management Server Mgmt-interface and has no dependency of the gateway.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which one of the following is a way that the objects can be manipulated using the new API integration in R80 Management?
A) Microsoft Publisher
B) JSON
C) Microsoft Word
D) RC4 Encryption
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
A) Distributed
B) Bridge Mode
C) Remote
D) Standalone
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server (Security Management Server) ?
A) Display policies and logs on the administrator's workstation.
B) Verify and compile Security Policies.
C) Processing and sending alerts such as SNMP traps and email notifications.
D) Store firewall logs to hard drive storage.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Fill in the blanks: The Application Layer Firewalls inspect traffic through the ________ layer(s) of the TCP/IP model and up to and including the ________ layer.
A) Lower; Application
B) First two; Internet
C) First two; Transport
D) Upper; Application
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The organization's security manager wishes to back up just the Gaia operating system parameters such as interface details, Static routes and Proxy ARP entries. Which command would be BEST suited to accomplish this task?
A) save configuration
B) backup
C) migrate export
D) upgrade export
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The IPS policy for pre-R80 gateways is installed during the _______ .
A) Firewall policy install
B) Threat Prevention policy install
C) Anti-bot policy install
D) Access Control policy install
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Showing 41 - 60 of 676
Related Exams