A) Create an AMI from the volume and share the AMI
B) Copy the data to an unencrypted volume and then share
C) Take a snapshot and share the snapshot with a friend
D) If both the accounts are using the same encryption key then the user can share the volume directly
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user is using the AWS SQS to decouple the services. Which of the below mentioned operations is not supported by SQS?
A) SendMessageBatch
B) DeleteMessageBatch
C) CreateQueue
D) DeleteMessageQueue
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization (Account ID 123412341234) has attached the below mentioned IAM policy to a user. What does this policy statement entitle the user to perform? 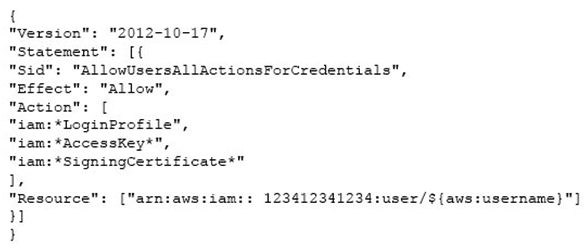
A) The policy allows the IAM user to modify all IAM user's credentials using the console, SDK, CLI or APIs
B) The policy will give an invalid resource error
C) The policy allows the IAM user to modify all credentials using only the console
D) The policy allows the user to modify all IAM user's password, sign in certificates and access keys using only CLI, SDK or APIs
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
The SysOps Administrator must integrate an existing on-premises asymmetrical key management system into an AWS services platform. How can the Administrator meet this requirement?
A) Implement AWS KMS and integrate with the existing on-premises asymmetrical key management system
B) Implement AWS CloudHSM and integrate it with the existing key management infrastructure
C) Deploy an Amazon EC2 instance and choose an AMI from an AWS partner in the AWS Marketplace
D) Create a master key in AWS KMS, and export that key to the existing on-premises asymmetrical key management system
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user has configured ELB with Auto Scaling. The user suspended the Auto Scaling AddToLoadBalancer (which adds instances to the load balancer. process for a while) . What will happen to the instances launched during the suspension period?
A) The instances will not be registered with ELB and the user has to manually register when the process is resumed
B) The instances will be registered with ELB only once the process has resumed
C) Auto Scaling will not launch the instance during this period due to process suspension
D) It is not possible to suspend only the AddToLoadBalancer process
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user has created a subnet in VPC and launched an EC2 instance within it. The user has not selected the option to assign the IP address while launching the instance. The user has 3 elastic IPs and is trying to assign one of the Elastic IPs to the VPC instance from the console. The console does not show any instance in the IP assignment screen. What is a possible reason that the instance is unavailable in the assigned IP console?
A) The IP address may be attached to one of the instances
B) The IP address belongs to a different zone than the subnet zone
C) The user has not created an internet gateway
D) The IP addresses belong to EC2 Classic; so they cannot be assigned to VPC
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization (Account ID 123412341234. has attached the below mentioned IAM policy to a user. What does this policy statement entitle the user to perform? 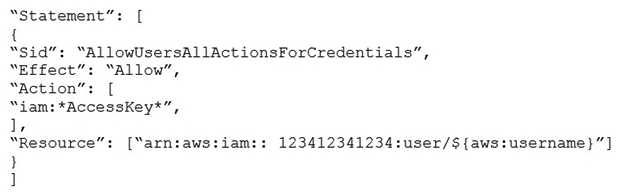
A) The policy allows the IAM user to modify all IAM users' access keys using the console, SDK, CLI or APIs
B) The policy allows the IAM user to modify all IAM users' credentials using the console, SDK, CLI or APIs
C) The policy allows the IAM user to modify all credentials using only the console
D) The policy allows the IAM user to modify the IAM user's own credentials using the console, SDK, CLI or APIs
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user has configured ELB with Auto Scaling. The user suspended the Auto Scaling terminate process only for a while. What will happen to the availability zone rebalancing process (AZRebalance. during this period?
A) Auto Scaling will not launch or terminate any instances
B) Auto Scaling will allow the instances to grow more than the maximum size
C) Auto Scaling will keep launching instances till the maximum instance size
D) It is not possible to suspend the terminate process while keeping the launch active
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An application hosted on AWS is going through an external compliance assessment. An Administrator has been tasked with providing proof of physical security at the facilities that are hosting the application. What should the Administrator do?
A) Work with AWS support to schedule a tour for the auditors.
B) Send a copy of the AWS Security whitepaper to the auditors.
C) Obtain a relevant report from AWS Artifact and share it with the auditors.
D) Find the address for the AWS Direct Connect facility on the AWS Website.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A financial service company is running distributed computing software to manage a fleet of 20 servers for their calculations. There are 2 control nodes and 18 worker nodes to run the calculations. Worker nodes can be automatically started by the control nodes when required. Currently, all nodes are running on demand, and the worker nodes are used for approximately 4 hours each day. Which combination of actions will be MOST cost-effective? (Choose two.)
A) Use Dedicated Hosts for the control nodes.
B) Use Reserved Instances for the control nodes.
C) Use Reserved Instances for the worker nodes.
D) Use Spot Instances for the control nodes and On-Demand Instances if there is no Spot availability.
E) Use Spot Instances for the worker nodes and On-Demand Instances if there is no Spot availability.
G) A) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company using AWS Organizations requires that no Amazon S3 buckets in its production accounts should ever be deleted. What is the SIMPLEST approach the SysOps Administrator can take to ensure S3 buckets in those accounts can never be deleted?
A) Set up MFA Delete on all the S3 buckets to prevent the buckets from being ddeleted.
B) Use service control policies to deny the s3:DeleteBucket action on all buckets in production accounts. Use service control policies to deny the s3:DeleteBucket action on all buckets in production accounts.
C) Create an IAM group that has an IAM policy to deny the s3:DeleteBucket action on all buckets in production accounts. Create an IAM group that has an IAM policy to deny the
D) Use AWS Shield to deny the s3:DeleteBucket action on the AWS account instead of all S3 buckets. Use AWS Shield to deny the action on the AWS account instead of all S3 buckets.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A sys admin is using server side encryption with AWS S3. Which of the below mentioned statements helps the user understand the S3 encryption functionality?
A) The server side encryption with the user supplied key works when versioning is enabled
B) The user can use the AWS console, SDK and APIs to encrypt or decrypt the content for server side encryption with the user supplied key
C) The user must send an AES-128 encrypted key
D) The user can upload his own encryption key to the S3 console
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company runs an application that uses Amazon RDS for MySQL. During load testing of equivalent production volumes, the Development team noticed a significant increase in query latency. A SysOps Administrator concludes from investigating Amazon CloudWatch Logs that the CPU utilization on the RDS MySQL instance was at 100%. Which action will resolve this issue?
A) Configure AWS Database Migration Service (AWS DMS) to allow Amazon RDS for MySQL to scale and accept more requests.
B) Configure RDS for MySQL to scale horizontally by adding additional nodes to offload write requests.
C) Enable the Multi-AZ feature for the RDS instance.
D) Modify the RDS MySQL instance so it is a larger instance type.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user has launched an EBS backed EC2 instance. The user has rebooted the instance. Which of the below mentioned statements is not true with respect to the reboot action?
A) The private and public address remains the same
B) The Elastic IP remains associated with the instance
C) The volume is preserved
D) The instance runs on a new host computer
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A SysOps Administrator has created an Amazon EC2 instance using an AWS CloudFormation template in the us-east-1 Region. The Administrator finds that this template has failed to create an EC2 instance in the us-west-2 Region. What is one cause for this failure?
A) Resources tags defined in the CloudFormation template are specific to the us-east-1 Region.
B) The Amazon Machine Image (AMI) ID referenced in the CloudFormation template could not be found in the us-west-2 Region.
C) The cfn-init script did not execute during resource provisioning in the us-west-2 Region.
D) The IAM user was not created in the specified Region.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company wants to increase the availability and durability of a critical business application. The application currently uses a MySQL database running on an Amazon EC2 instance. The company wants to minimize application changes. How should the company meet these requirements?
A) Shut down the EC2 instance. Enable multi-AZ replication within the EC2 instance, then restart the instance.
B) Launch a secondary EC2 instance running MySQL. Configure a cron job that backs up the database on the primary EC2 instance and copies it to the secondary instance every 30 minutes.
C) Migrate the database to an Amazon RDS Aurora DB instance and create a Read Replica in another Availability Zone.
D) Create an Amazon RDS Microsoft SQL DB instance and enable multi-AZ replication. Back up the existing data and import it into the new database.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user has developed an application which is required to send the data to a NoSQL database. The user wants to decouple the data sending such that the application keeps processing and sending data but does not wait for an acknowledgement of DB. Which of the below mentioned applications helps in this scenario?
A) AWS Simple Notification Service
B) AWS Simple Workflow
C) AWS Simple Queue Service
D) AWS Simple Query Service
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Does AWS offer any web-based graphic user interface to access and manage EC2 instances?
A) Yes, the AWS Application Clusters.
B) No, you can only use the available software development kits.
C) Yes, the AWS Management Console.
D) No, you can only use the command line interface.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
While creating the wait condition resource in AWS CloudFormation, a SysOps Administrator receives the error "received 0 signals out of the 1 expected from the EC2 instance". What steps should be taken to troubleshoot this issue? (Choose two.)
A) Confirm from the cfn logs that the cfn-signal command was successfully run on the instance.
B) Try to re-create the stack with a different IAM user.
C) Check that the instance has a route to the Internet through a NAT device.
D) Update the AWS CloudFormation stack service role to have iam:PassRole permission.
E) Delete the existing stack and attempt to create a new once.
G) C) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In Amazon CloudFront, if you have chosen On for Logging, the access logs are stored in _______________.
A) Amazon S3 bucket.
B) Amazon EBS.
C) Amazon Edge locations.
D) Amazon EC2 instance.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Showing 341 - 360 of 976
Related Exams